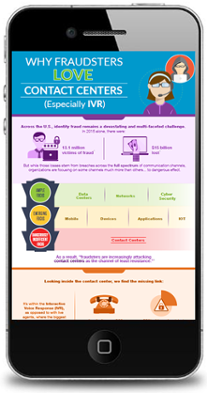
Since its inception in the 1950s, the contact center has been the cornerstone of company-customer relationships. It’s the keeper of personal customer information, the ambassador of the sales organization and a source of knowledge for marketing efforts. While many customers have a love-hate relationship with contact centers, it’s still the place they turn to when they have a problem. How the contact center responds will dictate whether that customer sticks around or becomes an ex-customer. Essentially, the customer's relationship with the contact center strongly influences the trust in the customer relationship.
Since its inception in the 1950s, the contact center has been the cornerstone of company-customer relationships. It’s the keeper of personal customer information, the ambassador of the sales organization and a source of knowledge for marketing efforts. While many customers have a love-hate relationship with contact centers, it’s still the place they turn to when they have a problem. How the contact center responds will dictate whether that customer sticks around or becomes an ex-customer. Essentially, the customer's relationship with the contact center strongly influences the trust in the customer relationship.
Don't let contact center fraud undermine customer relationships. While it may seem like an age-old problem that was solved long ago with a few precautions, the truth is that contact center fraud is on the rise again. You’d never know it from reading the business headlines, however: those are all reserved for cybersecurity threats.
Security’s Great Eye is Focused on Networks and Cybersecurity
Ah, the memories:
Most of this occurred long before any of us had logged into our slow dial-up connection to retrieve our email from AOL or Netscape.
- While few of us were using the Internet back in 1986, it was a noteworthy year for it: the very first computer virus, nicknamed “Brain,” began infecting computers running MS-DOS.
- In 1991, Kevin Poulsen became the first computer hacker ever arrested after spending years on the lam.
- In the 1990s, the Internet community saw the “Melissa” virus and heard about distributed denial of service attacks.
- In the 2000s, we lived through “Nimda” and became aware of the earliest phishing scams.
Since those days, cybersecurity has become a global powerhouse industry. A recent report by Cybersecurity Ventures estimated that the global cybersecurity industry will grow from $75 billion in 2015 to $170 billion by 2020. As the “Internet of Things” ramps us – networked devices all over the world programmed to communicate with one another through data, video and text – cyber-criminals will set their sights on bigger targets, such as electric grids, power plants, smart cars and mobile networks.
But while the world frets about cyber security, who’s guarding the other channels cyber-thieves can use to gain personal information?
While Customer Care Goes Cross-Channel, So Too Does Fraud
Before the Internet, fraud was generally conducted in person, by mail or over the telephone. Nigeria scams aren’t new: prior to the digital age, these attempts to gain access to trusting peoples’ bank accounts arrived by mail. Later, with the advent of automated dialers, they came in by telephone.
“Fraud by contact center” is an old concept – it used to be the front door for thieves – but it’s experiencing a resurgence as companies devote most of their money and efforts defending the back door.
Ignoring the Contact Center in Lieu of Securing….
- Cybersecurity: What every business needs to know
- Networks: The biggest security threats we’ll face in 2016
- Data centers: How to build physical security into a data center
- Applications: 10 most common app attacks in action
- Devices: 13 principles to ensure enterprise system security
- Mobile: mobile app security-4 critical issues
- Internet of Things: IoT security challenges and concerns
There’s no doubt that there is a lot of work to be done – especially in the IoT and mobile channel where fraud measures are in the early days and incomplete. In the meantime, criminals are sneaking back around to the unguarded front door.
Fraudsters Like Self-Service, Too
To a persistent criminal -- whether it’s a solo bad actor or someone part of a larger organization - the interactive voice response (IVR) is a tempting target. With a little personal information on a target victim and a lot of patience, fraudsters can call in repeatedly and try to gain more personal data with each attempt.
Since the IVR is perceived to be a less monitored channel, it has gained a reputation as a location of easy ingress, particularly if the fraudster is in possession of some personal information that’s been gained from other channels such as social media, data breaches, mail theft, malware and more. Armed with a few nuggets of information, it becomes easier for a criminal to “test” the contact center IVR and build up a data profile of the target before engaging in a full-fledged account takeover.
 It’s pretty easy for thieves to do:
It’s pretty easy for thieves to do:
In many cases, the IVR may be completely unguarded and unmonitored, and has become a playground for perpetrators to commit fraud with the assumption that there are no eyes them.
Smart companies need to begin closing the gap between cybersecurity and contact center security, and the way they’ll do it is with actionable intelligence and some lessons gleaned from the methods being used to protect networks.
Putting a Watchdog Back on Contact Center Channels
Analytics and monitoring are two of the most prominent tools being used for cybersecurity today: IDC has reported that the hottest areas of growth going forward will be security analytics and threat intelligence, which involves keeping track of vulnerabilities and criminal attempts discovered through network monitoring. Knowledge is also power when it comes to the contact center, and analytics and monitoring have an important role to play there, too.
 An IVR with multi-layered fraud prevention is a unique technology that solves a problem many companies don’t even realize they have. As the contact center’s first line of defense, it provides the kind of one-of-a-kind automated, multi-layered fraud management that self-service environments require if they’re to be secure.
An IVR with multi-layered fraud prevention is a unique technology that solves a problem many companies don’t even realize they have. As the contact center’s first line of defense, it provides the kind of one-of-a-kind automated, multi-layered fraud management that self-service environments require if they’re to be secure.
Done right, this type of solution can:
- Spot fraudulent activity in the IVR
- Raise red flags in real time
- Take action to prevent an attack before loss occurs
Catch Fraud Before It Happens
Too often today, malicious activity in the contact center is caught downstream, or AFTER the criminal has stolen money or personal data. The resulting mess and clean up can take months or even years. The focus going forward should be to identify ways of stopping the fraud upstream before it can have a negative effect on the customer experience.
In the next post in this series, we’ll discuss ways that contact centers can use fraud prevention in the IVR to spot – and end – suspicious activity upstream in real-time, all while ensuring that security processes don’t become too onerous for existing customers.
After all, the point is to keep the criminals out of your customers’ information…not the customers themselves.
Download this Infographic >